Introduction
When it comes to securing sensitive applications and data, a best practice is to encrypt the data. While encrypting data-at-rest and data-in-motion are well-recognized issues with multiple solutions, runtime application security has been an unsolved problem. Plain text code and data is exposed at runtime, and that information can include sensitive data, keys for data-at-rest and certificates for data-in-motion.
Confidential Computing with the Anjuna Seaglass Platform augments the architecture provided by Intel® Software Guard Extensions (Intel® SGX). Anjuna SGX Runtime provides runtime protection for sensitive applications and their data. It offers the following main benefits:
-
Security for the application regardless of the state of infrastructure security.
-
Simplicity - requires no code changes or recompilation, and seamlessly integrates into existing DevOps processes.
It uses the following constructs to provide security:
- Memory Isolation
-
Completely isolates application memory from anything else on the machine including the operating system. Memory never leaves the CPU secure enclave unencrypted. No one can access memory, not even with root or physical access to the system.
- Remote Attestation
-
Ensures a secure trusted channel to a back-end server application, provides integrity by validating that expected code is running in the expected environment.
These constructs are provided by Secure Enclaves, implemented in modern processors.
Secure enclaves
Conventional approaches to securing applications have relied primarily on software to provide protection. However good the software implementation may be, an attacker that is able to gain privileged access would conceivably be able to circumvent software defenses. A recent and disruptive technology introduced in many new processor models provides a better security and privacy model. It allows you to run an application in an environment that is isolated from the host, while running on the same machine. In the case of Intel®, the key enabler is the hardware-level memory isolation introduced by Intel® Software Guard Extensions, which creates an encrypted partition of the memory. Somewhat similar functionality is offered by AMD in the form of Secure Encrypted Virtualization (SEV).
Intel® SGX brings a hardware root-of-trust and program isolation to commodity processors, enabling the handling of sensitive data in a trusted execution environment called a secure enclave.
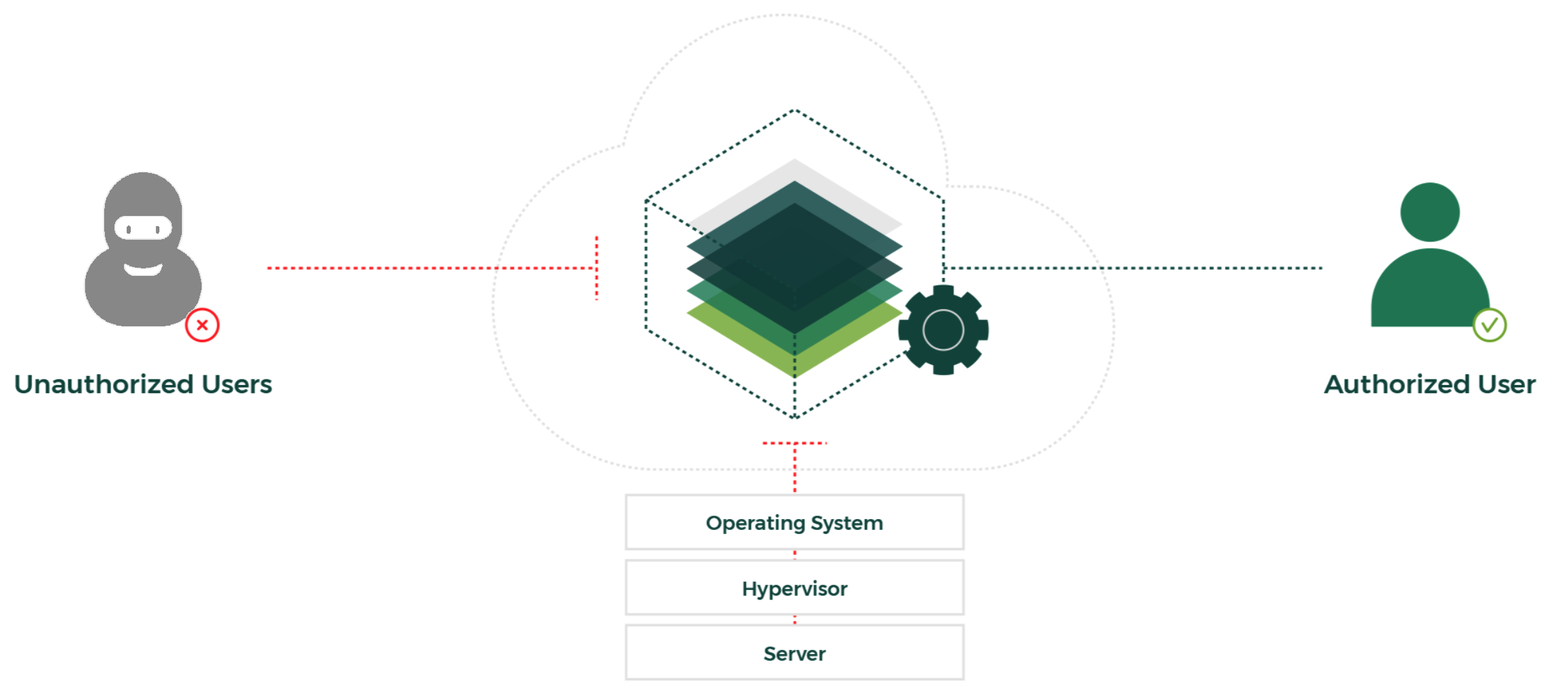
Secure enclaves enable running an application so that its contents and the data it handles are completely inaccessible to any other entities. These “blocked” entities include privileged users on the guest OS, the hypervisor, or the host OS itself.
About this document
This guide is structured as follows:
-
Concepts explains some high-level concepts important when working with secure enclaves.
-
Getting the Anjuna SGX Runtime explains how to obtain and set up the Anjuna Runtime.
-
First steps guides you through running a few simple programs with the protection of a secure enclave.
-
Configure applications to work with the Anjuna SGX Runtime shows you how to configure the Anjuna Runtime to work effectively with your applications.
-
Secure inputs and outputs explains how you can configure the Anjuna Runtime to automatically protect input and output data.
-
Tutorial: Anjuna in a Docker container shows how to create a Docker container that can run applications in a secure enclave.
-
Advanced: The Anjuna Policy Manager describes how to set up the Anjuna Policy Manager, a tool that helps you manage encryption and signing keys.
-
Advanced: Trusting the software in production explains how you can trust software running in a secure enclave.
-
Anjuna SGX Runtime Python package describes how to use the Python package that Anjuna provides.
-
The Glossary of terms defines words and phrases used in this document with technical or specialized meanings.
-
The Command reference is a reference to the command-line tools distributed with the Anjuna software.
-
The Configuration reference explains the configuration options used to control the behavior of the Anjuna Runtime.
-
The Syscall reference describes custom syscalls implemented by the Anjuna SGX Runtime.
-
The Troubleshooting section addresses warnings and errors you might encounter while using Anjuna.
Document conventions
This section describes typographical and other conventions used in this guide.
You can find definitions of specialized vocabulary in the Glossary of terms.
Text colored like this is a link to another document, either in this guide or elsewhere on the web.
Text in monospace type represents text that appears in a terminal or in the filesystem of a host.
Commands and files used by the Anjuna SGX Runtime and example code are shown in monospace type.
A block of text in monospace type represents an interaction with a host’s shell in the terminal, or the text of a file.
This block of text is an example of monospace type used to illustrate the contents of a file.
Some code blocks are shortened to emphasize only the relevant configuration.
A line with <snip>… indicates that some lines have been removed from the full configuration.
The following text illustrates the appearance of a command in a terminal shell. You can copy the text by hovering over it and clicking on the clipboard icon to the right.
$ ls -alText in <angle brackets> in examples stands for text to be replaced.
For example, in this text:
/home/<username>/.bashrc
replace <username> with an actual username.
Tabs represent different versions of instructions for different platforms. Usually you will only need to run the version for your current platform.
For example, the following tabs represent different Dockerfile base images depending on your Ubuntu version.
-
Ubuntu 18
-
Ubuntu 20
FROM ubuntu:18.04FROM ubuntu:20.04